PSA: Stop using your phone number for two-factor authentication — here's why
How your old phone number allows attackers to hold you hostage

Two-factor authentication is everywhere. From the moment you sign in to your Gmail account to accessing your financial details via PayPal, 2FA is there to greet you as a more secure way of logging in. You’ll even find it when setting up a PS5 or Xbox Series X. Heck, chances are, you’ve already used to today.
Also known as multi-factor authentication, 2FA is an extra layer of security — used by virtually every online platform — that stops many low-level hackers in their tracks, protecting all your valuable private information from being breached.
- The best phone deals in 2021
- Find out the best smartphones in 2021
Alas, hacking tactics are forever evolving, and all it takes is one crafty cybercriminal to find a tiny hole in the armor and plunder what were once impenetrable accounts to their heart’s content. But you don’t have to be a whizz at decrypting code to gain access to an unsuspecting victim’s account.
In fact, according to the 2021 Verizon Data Breach Investigations Report, 61% of the 5,250 confirmed security breaches the American network operator analyzed involved stolen credentials. Of course, multi-factor authentication’s purpose is to prevent malicious actors from gaining access to an account even if they discover a super-secret password.
But much like how Scar left Mufasa to fall to his doom in one of the greatest betrayals of all time, the security method can also be the root cause of cybercriminal activity. The real traitor? Your old phone number.
For a better sense of how attackers can easily use two-factor authentication against you, it’s best to know what the online security method is and how it works. If it helps, think of your old phone number as Scar throughout this piece.
What is two-factor authentication?
Multi-factor authentication (MFA) is a digital authentication method used to confirm the identity of a user to allow them access to a website or app through at least two pieces of evidence. Two-factor authentication, more popularly known as 2FA, is the most commonly used method.
In order for 2FA to work, a user must have at least two important pieces of credentials in order to log in to an account (with multi-factor usually involving more than three different details). This means if an unauthorized user gets their hands on a password, they will still need access to an email or phone number linked to the account where a special code is sent for an extra level of protection.
For example, a bank will require a username and password in order for a user to access their account, but it also needs a second form of authentication such as a unique code or fingerprint recognition to confirm a user’s identity. This second factor can also be used before a transaction is made.
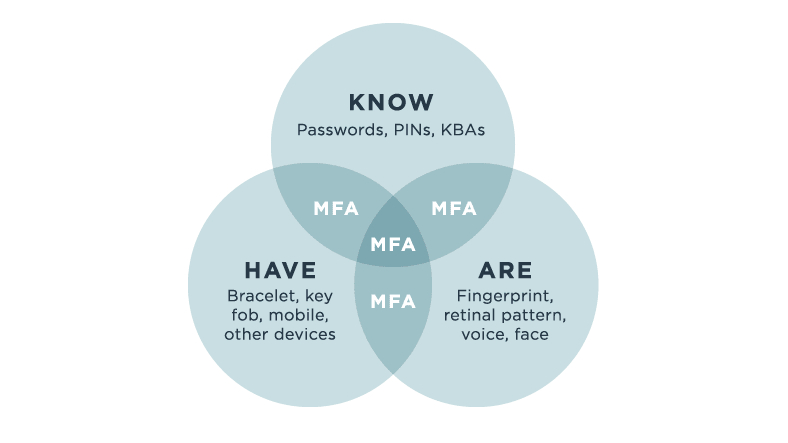
As explained by software company Ping Identity, 2FA’s required credentials are split into three different categories: “what you know”, “what you have”, and “what you are.” In terms of “what you know”, or your knowledge, this comes down to your passwords, PIN number, or answer to a security question such as “what is your mother’s maiden name?” (something I never seem to remember).
“What you are” is arguably the most secure category, as it confirms your identity from a physical trait unique only to you. This is usually seen on smartphones, such as an iPhone or Samsung Galaxy phone, using biometric authentication such as a fingerprint or facial scan to gain access.
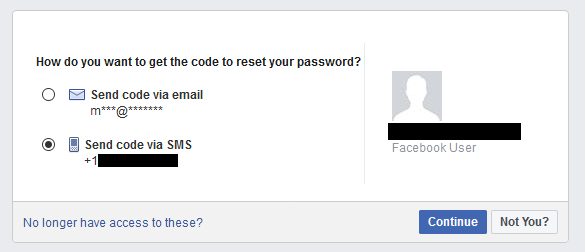
As for “what you have”, this refers to what is in your possession, which can be anything from a smart device to a smartcard. Generally, this method means getting a pop-up notification on your phone via SMS that needs to be confirmed before gaining access to an account. For any professionals using Google Gmail for business, you’ll have come across this category.
Unfortunately, that last category is cause for concern, especially when you throw phone number recycling into the mix.
Phone number recycling
According to the Federal Communications Commission (FCC), more than 35 million numbers in the U.S. are disconnected and become available again by reassigning them to a new subscriber every year. Sure, numbers are infinite and all, but there are only so many 10 or 11-digit combinations a mobile network can offer its customers.
The U.K.’s Office of Communications (Ofcom), the entity that assigns mobile numbers to U.K. network providers, states (via The Evening Standard) that it has a strict “use it or lose it” policy for pay-as-you-go mobile numbers. Vodafone disconnects and recycles a phone number after just 90 days of no activity, while O2 does this after 12 months.
In the U.S., network providers including Verizon and T-Mobile let customers change and choose the available numbers shown on online number change interfaces via their website or app. There are millions of recycled phone numbers available, with more piling up each day.
Recycled numbers can be harmful to those who originally owned them, as many platforms, including Gmail and Facebook, are linked to your mobile number for password recovery or, and here’s the kicker, two-factor authentication.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
How 2FA puts you at risk
A study at Princeton University discovered how easily anyone can obtain a recycled phone number and use it for several common cyberattacks, including account takeovers and even denying access to an account by holding it hostage and asking for a ransom in exchange for access.
According to the study, an attacker can find available numbers and check if any of them are associated with online accounts from previous owners. By viewing their online profiles and checking to see if their old number is linked, attackers can buy the recycled number (just $15 at T-Mobile) and reset the password on the accounts. Using 2FA, they will then receive and enter the special code sent via SMS.
The researchers tested 259 numbers they obtained through the two U.S. mobile carriers and found that 171 of them had a linked account on at least one of six commonly used websites: Amazon, AOL, Facebook, Google, PayPal, and Yahoo. This is called a “reverse lookup attack.”
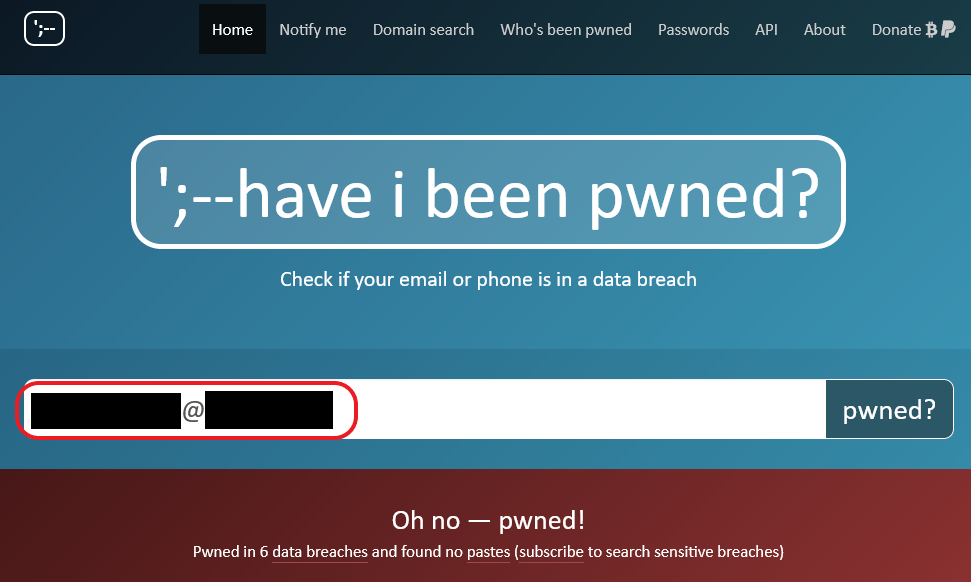
Researchers found another variation of the attack that allowed malicious actors to hijack accounts without having to reset a password. Using online people search service BeenVerified, a hacker could search for an email address by using a recycled phone number, then check if the email addresses had been involved in data breaches using Have I Been Pwned?. If they had, the attacker could buy the password on a cybercriminal black market and break into a 2FA-enabled account without needing to reset a password.
To make matters worse, attackers can also take your account hostage. A nasty trick sees a hacker obtain a number to sign up to several online services that require a phone number. Once complete, they discontinue the service so the number can be recycled for a new subscriber to start using. When the new user tries to sign up for the same services, the hacker will be notified via 2FA, and deny them a way to use the service. The threat actor will then ask for the victim to pay a ransom if they want to use these online services.
Using 2FA in this way is atrocious, but that doesn’t stop it from happening. T-Mobile reviewed the research back in December, and now reminds subscribers to update their contact number on bank accounts and social media profiles on its number change support page. But that’s all the carrier has the power to do, meaning those not informed will be open to attacks.
Alternate ways to use 2FA
If anything, phone numbers and 2FA don’t gel very well. The good news, however, is that there are now more options available when opting to use 2FA, including the aforementioned biometric methods or authenticator apps.
However, these options aren’t always available, and sometimes, online services only provide you two options for 2FA: your phone number or your email address. If you don’t want hackers rummaging through your private information, it’s best to opt for email authentication. Of course, there are those who don’t always use their emails, and with time, can often forget their passwords. No password, means no way of obtaining an authentication code.
To solve this, it’s best to find a password manager. LastPass used to be the go-to for years thanks to its free-tier service, but there are other contenders worth checking out.
“But what if I’m already using my phone number for 2FA?” I hear you ask. If you’re considering changing your phone number, make sure to unlink your phone number from the online services it is connected to before making the switch. And, if you have already made the switch, it is well worth your time updating your accounts to get rid of any Scars (phone numbers) lying in wait to backstab you when you least expect it.
Outlook
Two-factor authentication is everywhere, and it’s here to stay. In fact, Google will soon force you to use 2FA when signing in, with the tech giant vouching for a “safer future without passwords.” This is not a terrible idea, but there’s potential for many people to use their phone numbers as a way to be identified. We’re sure low-level hackers like the sound of that.
To prevent any of this from happening, once 2FA starts taking over all online platforms, all you have to do is, well, read the title of this article and follow our advice.

Darragh Murphy is fascinated by all things bizarre, which usually leads to assorted coverage varying from washing machines designed for AirPods to the mischievous world of cyberattacks. Whether it's connecting Scar from The Lion King to two-factor authentication or turning his love for gadgets into a fabricated rap battle from 8 Mile, he believes there’s always a quirky spin to be made. With a Master’s degree in Magazine Journalism from The University of Sheffield, along with short stints at Kerrang! and Exposed Magazine, Darragh started his career writing about the tech industry at Time Out Dubai and ShortList Dubai, covering everything from the latest iPhone models and Huawei laptops to massive Esports events in the Middle East. Now, he can be found proudly diving into gaming, gadgets, and letting readers know the joys of docking stations for Laptop Mag.