How to find and remove stalkerware on iPhone — protect your privacy
Protect yourself from digital stalking

If you’ve been reading the news lately, you might have been hearing a lot about stalkerware, but what is it exactly? Stalkerware is any app or tool that allows someone to spy on you without your knowledge. It’s particularly prevalent on phones, including the iPhone, due to the wealth of data available through your phone.
I’m going to walk you through how to find and eliminate stalkerware on your iPhone and then how to protect yourself from stalkerware before it is installed.
How to find stalkerware on your iPhone and eliminate it
While the Apple App Store has a better track record on keeping out stalkerware than Android, it isn’t flawless, so using an iPhone alone doesn’t guarantee your safety. However, iOS does have a number of tools that make it easier to identify stalkerware on your phone.
I’ll start with the most aggressive example and then address stalkerware that is slightly harder to find.
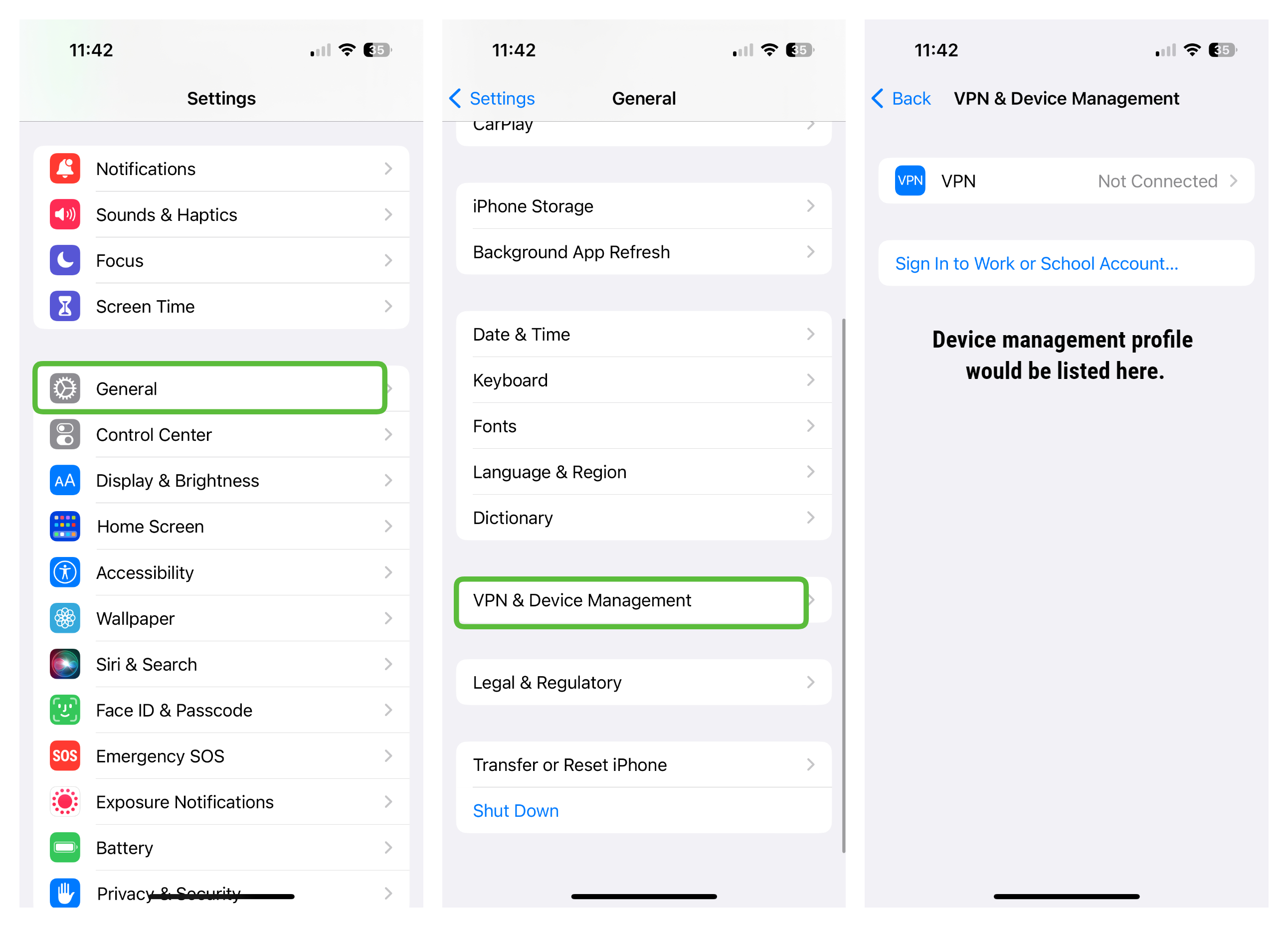
Device Management Profiles
If the stalker is looking to monitor your every action on the iPhone, then one of the most common methods is to use a device management profile. While that won’t be outwardly obvious as you use your phone, you can easily see if one is in place by going to Settings > General > VPN & Device Management. On this screen, you will see any profiles installed on your phone. There are legitimate uses for this, of course (e.g.,you may have one from school or work), but just check to be sure you recognize any profiles listed there. If there are any that you can’t identify, simply tap on them and delete them.
Jailbroken iPhone
With Apple building so many protections into iOS to prevent stalkerware and other problematic apps from being installed on your iPhone, a stalker may jailbreak your iPhone in order to install illegal apps. Again, this won’t be easy to spot as you use your phone, but look for any apps you don’t remember installing on your phone, including an app called Cydia, an Apple App Store alternative often used by jailbreakers. Attempting to update a known app will also be a giveaway as it won't be able to connect to the App Store for the update.

Search for unknown apps
Apple does a lot to prevent stalkerware from making it into the App Store, but it is possible for things to slip through or for legitimate apps to be misused as stalkerware. One example is parental control apps, which are designed to allow parents to help keep their children safe online, but those same features can be abused by a stalker. Swipe right on your iPhone home screen until you get to the App Library and tap in the search box at the top of the screen. Scroll through all of your installed apps and make sure that there is nothing there that you don’t recognize.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
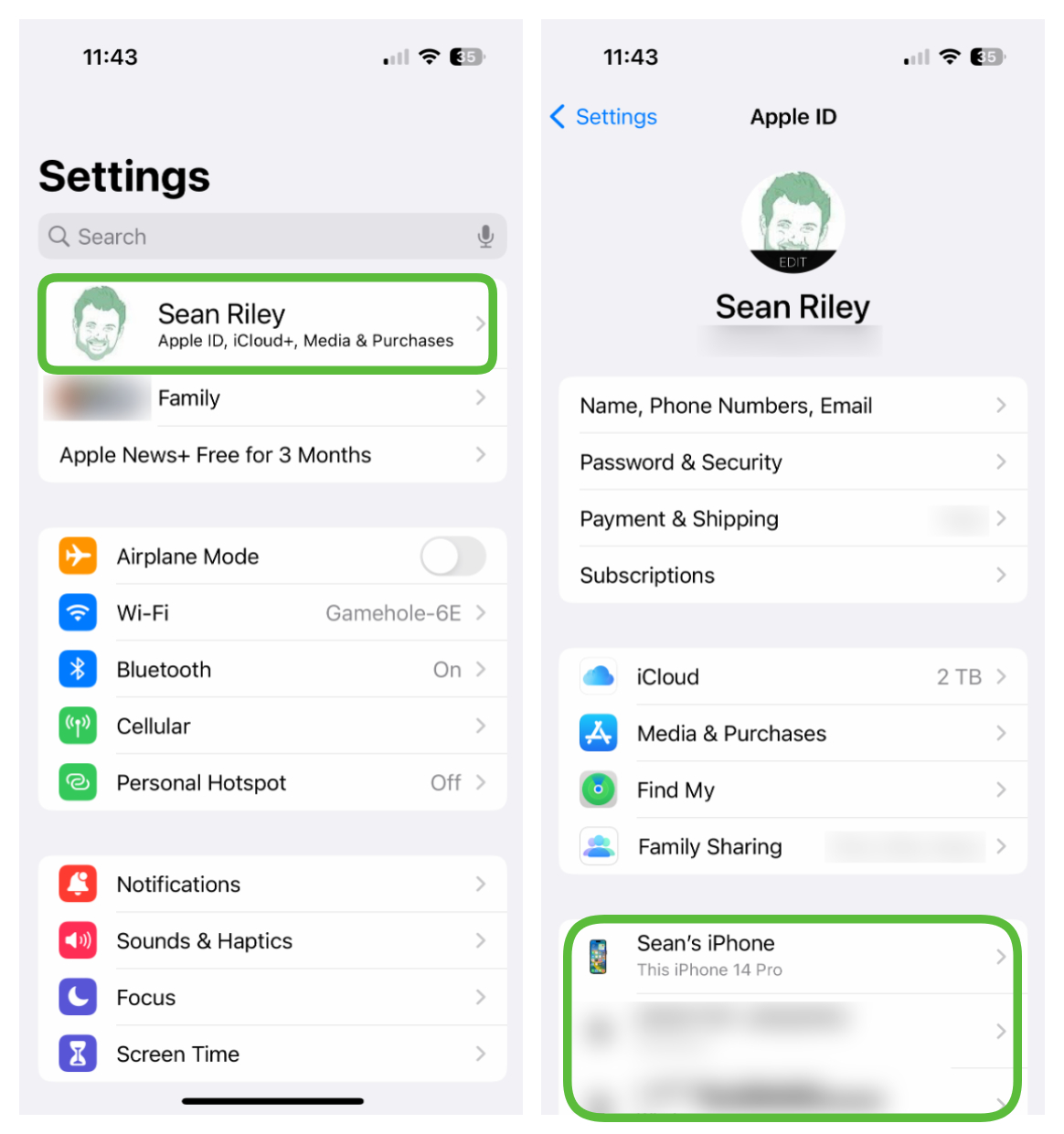
Check your Apple account
Apple’s own tools can be misused as well, so check to make sure that you know exactly who has access to any of your data through your Apple account.
First, open the Find My app. Apple’s helpful tool can be used to track your own devices if they get lost or allow you to keep tabs on friends and family. Naturally, that can also be misused by a stalker so you want to verify who has access to your location. Simply look at the list in the People tab of the Find My app, and if there’s anyone that you don’t want to be sharing your location with, tap on them and tap either “Stop Sharing My Location” or “Remove [Name]” and they will no longer be able to track you.
To verify that the data in your Apple account isn’t being viewed by anyone else, go to Settings and tap on your name at the top of the screen. There are potentially two areas that you want to check here: your registered devices and a Family Sharing Group. You will only see a Family Sharing Group listed if you are in one, so if you don’t see it, then don’t worry about it.
Scroll down the page and see if your Apple ID is logged into any devices other than your own and if so simply tap on them and select “Remove from Account.” If you have a listed Family Sharing Group that you don’t wish to be a part of, just tap on your own name and then select to remove yourself.
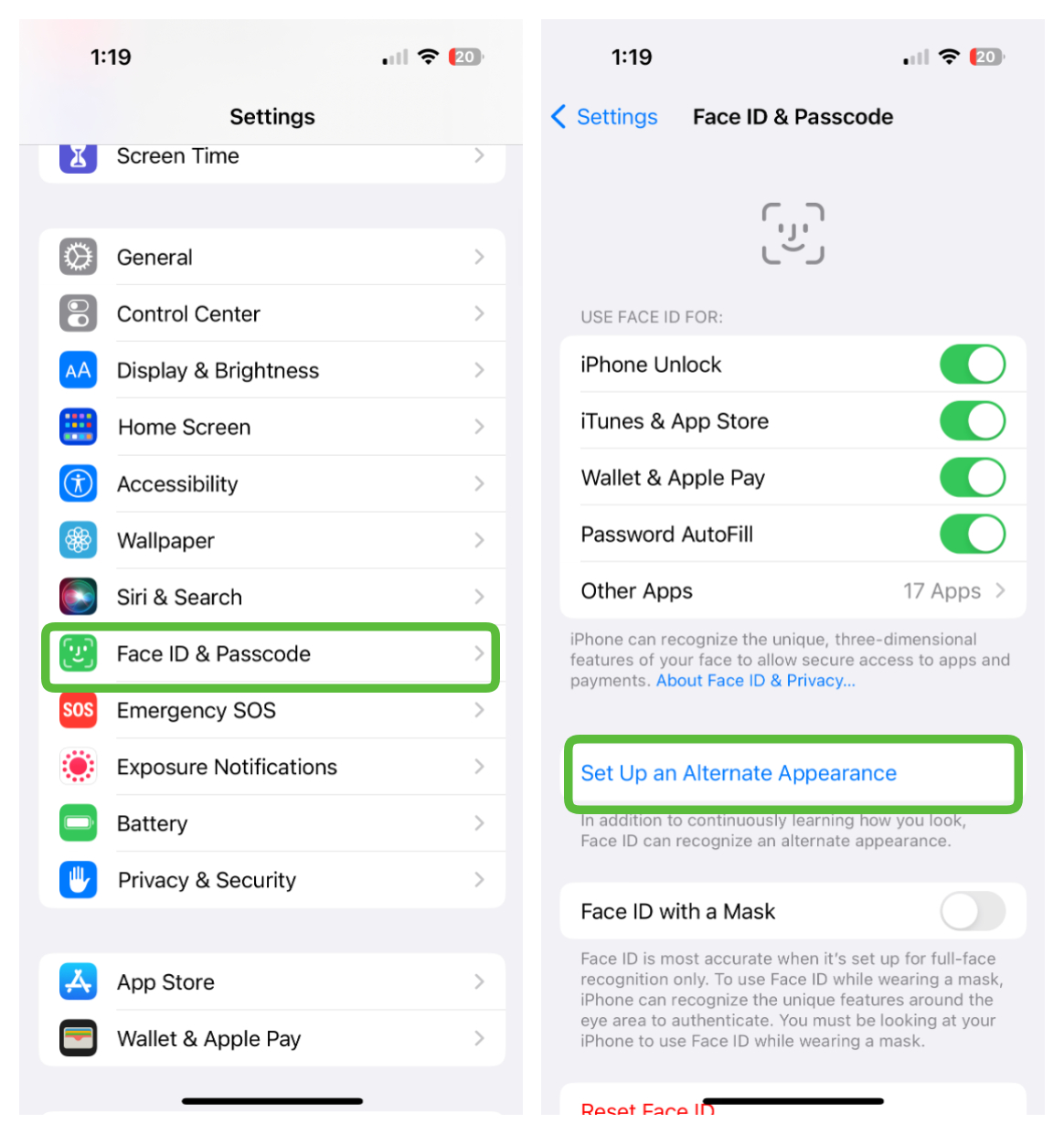
How to protect your iPhone from stalkerware
Stalkerware is almost universally dependent on getting direct access to your device in order to set it up, so the best protection is to make sure that no one else can log in to your iPhone. Once again, Apple offers you a variety of tools that will make this easy for you.
The first is to use Touch ID or Face ID for your login. Now there are two caveats here; one is that you still need a passcode or password as backup. The second is that you should check to make sure no one has added their own fingerprint or face to your phone prior to you ensuring that it is locked down.
To do this go to Settings > Face ID & Passcode (Touch ID & Passcode on some iPhones and iPads). Now look for an Alternate Appearance set up for Face ID login or in the case of Touch ID an additional fingerprint. You can reset Face ID or reset Touch ID if you want to start from a clean slate.
Now for the passcode, we’ve covered before why you should switch from a passcode to an iPhone password, it makes your iPhone completely unhackable even if someone steals your iPhone. Take a look at that article for further instructions on how to switch to a password along with recommendations on how long it should be.
If you followed all of the aforementioned steps, you should feel confident that your iPhone is stalkerware free and safe from future attempts to install stalkerware.
Stalkerware is often used in cases of domestic abuse. For anonymous and confidential help, the National Domestic Violence Hotline can be reached 24/7 at 1-800-799-7233.
Sean Riley has been covering tech professionally for over a decade now. Most of that time was as a freelancer covering varied topics including phones, wearables, tablets, smart home devices, laptops, AR, VR, mobile payments, fintech, and more. Sean is the resident mobile expert at Laptop Mag, specializing in phones and wearables, you'll find plenty of news, reviews, how-to, and opinion pieces on these subjects from him here. But Laptop Mag has also proven a perfect fit for that broad range of interests with reviews and news on the latest laptops, VR games, and computer accessories along with coverage on everything from NFTs to cybersecurity and more.

