How to Scan External Drives for Malware in Windows 8
News
By
Konrad Krawczyk
published
Join the conversation
Add us as a preferred source on Google
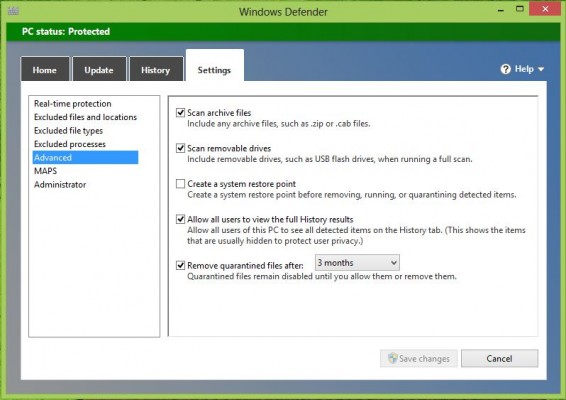
We're comfortable with Windows Defender safeguarding our systems while we surf the web in Windows 8. However, malware can also make its way onto your system if you plug in an infected external drive or USB key. Prevent such situations from occurring by using Windows Defender to scan external storage devices.
1. Click the Settings tab in Windows Defender.
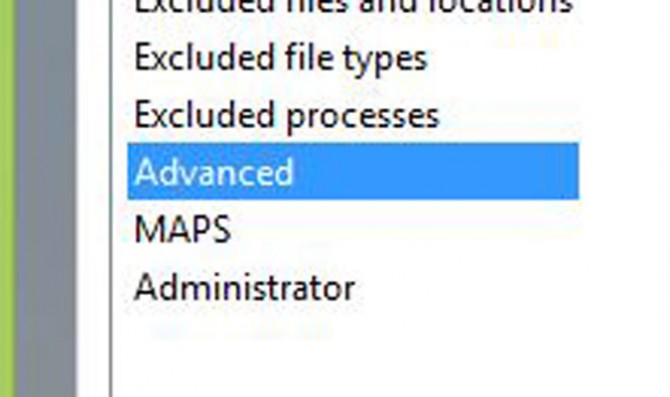
2. Select Advanced.
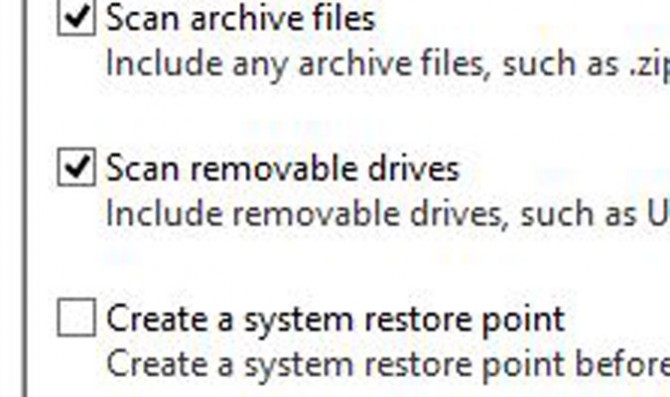
3. Check Scan Removable Drives.
4. Click Save changes.
Get The Snapshot, our free newsletter on the future of computing
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
MORE FROM LAPTOP MAG...