Massive Mac Security Flaw Gets Root in Seconds
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You are now subscribed
Your newsletter sign-up was successful
A very simple task will let anyone gain permanent root access to Macs running macOS 10.13 High Sierra, earning easy access to all settings and data.
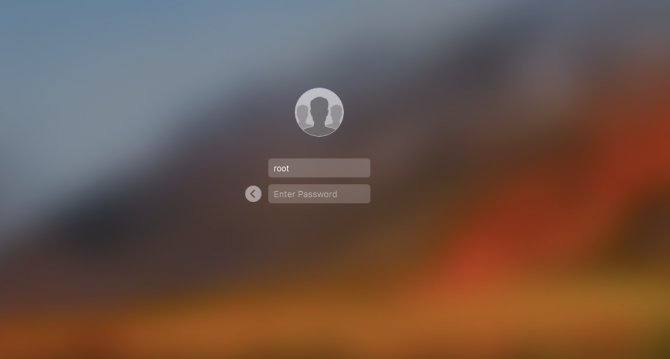
First disclosed on Twitter earlier today (Nov. 28) by Turkish app developer Lemi Orhan Egan, the bug lets anyone, not just users with administrator privileges, get into System Preferences by clicking on the lock and typing in "root" as the username and leaving the password blank.
Update 6:33 pm ET: Apple has issued the following statement, as reported by MacRumors:
"We are working on a software update to address this issue. In the meantime, setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, please follow the instructions here: https://support.apple.com/en-us/HT204012. If a Root User is already enabled, to ensure a blank password is not set, please follow the instructions from the 'Change the root password' section."
What You Should Do Now
One way to prevent this sort of access would be to enable root access on your own and give the root account a password. Then you can go to the terminal to an type "dsenableroot -d" (without quotes) to turn off root access. Anyone who tries to get in this way won't have the right password. If you want to turn root access back on, type "dsenable root" in the terminal.
MacRumors also has step-by-step instructions on how to prevent admin access to your Mac you can follow right now.
Why You Should Be Worried
This root access bug creates a new user profile that presents itself as "Other" on the Mac's primary login screen. Type in "root" as the username, type in nothing for the password, and you will open an account with complete root access.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You can access it via System Preferences>Users & Groups>Click the lock to make changes. Then use "root" with no password. And try it for several times. Result is unbelievable! pic.twitter.com/m11qrEvECs — Lemi Orhan Ergin (@lemiorhan) November 28, 2017
We tested this procedure on both an old MacBook Pro and the latest MacBook Air, each running High Sierra. In both cases, we were able to run routine "periodic" diagnostic commands that would usually require temporary "sudo" privileges and an administrator's password -- but this time, with no "sudo" request or admin credentials at all.
On Twitter, Apple Support wrote to Egan: "Thanks for reaching out. Send us a DM, and we'll look further into this with you."
We reached out to Apple ourselves but did not hear back immediately. We will update this story if we receive a response.
This is a massive security issue, as it would permit anyone to easily seize control of your laptop if they had even brief physical access. Even worse, this secret is now completely out in the open. Generally, flaws like this are disclosed privately to the company so they can be fixed without anyone taking advantage.
Apple Laptop Guide
Andrew is a contributing writer at Laptop Mag. His main focus lies in helpful how-to guides and laptop reviews, including Asus, Microsoft Surface, Samsung Chromebook, and Dell. He has also dabbled in peripherals, including webcams and docking stations. His work has also appeared in Tom's Hardware, Tom's Guide, PCMag, Kotaku, and Complex. He fondly remembers his first computer: a Gateway that still lives in a spare room in his parents' home, albeit without an internet connection. When he’s not writing about tech, you can find him playing video games, checking social media and waiting for the next Marvel movie.