This Microsoft app can host malware that remotely accesses your webcam, takes screenshots — what to do
Watch out for that OneNote attachment!

Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You are now subscribed
Your newsletter sign-up was successful
Word and Excel used to be hackers' favorite apps for distributing malicious software to hoodwinked victims who were baited into downloading email attachments, but Microsoft eventually blocked the exploit in July. So what now?
According to BleepingComputer, threat actors are using another Office platform: OneNote. Hackers are using the productivity app to remotely control victims' PCs, allowing them to install more malware, breach cryptocurrency wallets, steal passwords — and even take screenshots and access your webcam.
How hackers are using OneNote to wreak havoc on PCs
On the plus side, in order to be a victim of a OneNote-propelled attack, you'd need to fall for a phishing email campaign. And we'd hope that the egregious spelling errors, suspicious-looking email address, and poor mimicking of an official company would deter you from falling for it, but alas, hackers seem to snag a few victims into its web nonetheless.
During BleepingComputer's investigation, it found that cybercriminals masked their ill-intentioned, malware-infested emails as official DHL correspondence. The emails attempted to fool recipients into thinking they were getting DHL invoices, ACH remittance forms, shipping documents, notifications, and more.
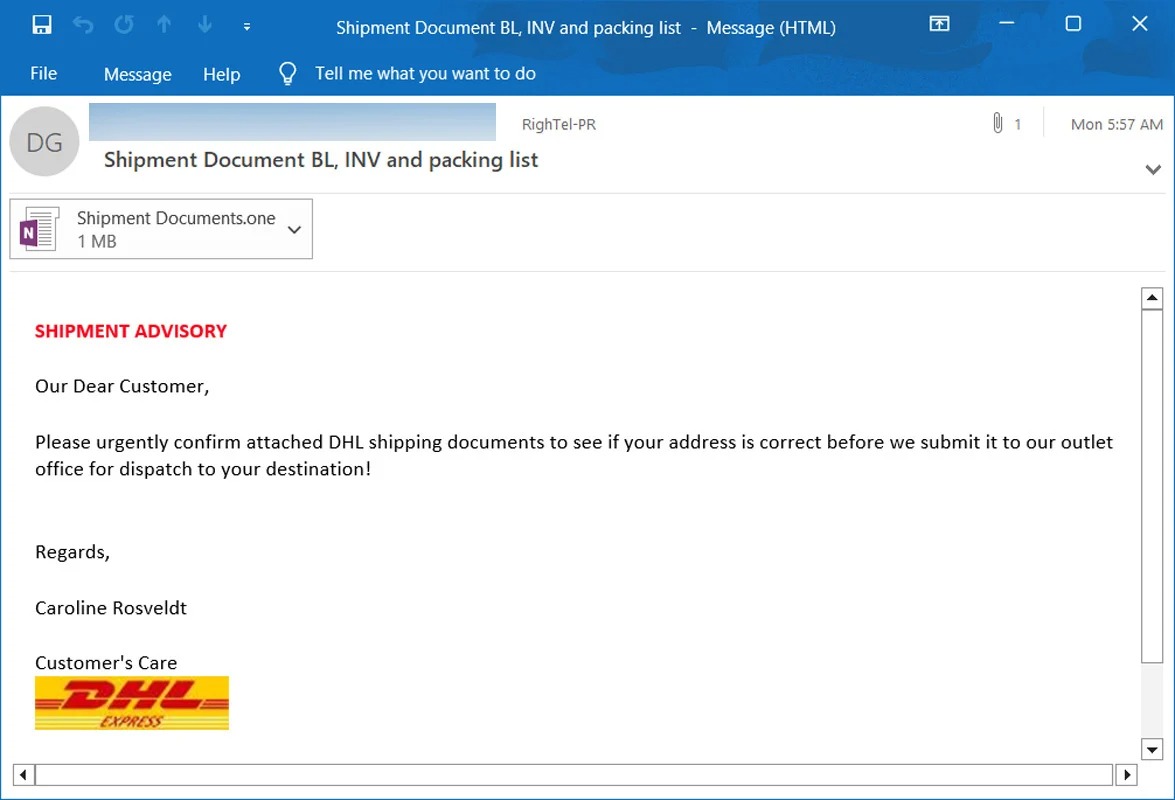
Once a victim clicks on the OneNote attachment, the information is blurred. There's an overlay that says, "Double Click to View File." If the quarry follows the instruction, chaos ensues.
"Threat actors are [...] attaching malicious VBS attachments that automatically launch the script when double-clicked to download malware from a remote site and install it," BleeingComputer said.
Remote-access trojans will then take over the computer, allowing hackers to steal victims' files. breach cryptocurrency wallets, and snatch browser passwords. In some cases, cybercriminals can even take screenshots and take control of users' webcams.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
How to protect yourself
Good news! If you attempt to download a malicious attachment, according to BleepingComputer, you should get a warning from Windows informing you that the document may be harmful. However, users often ignore this pop-up message and download it anyway — don't be that person.
But you shouldn't get that far, really, because you should refrain from opening emails and attachments from unknown sources. Plus, phishing emails are typically easy to spot. As mentioned, poor grammar, spelling errors, waywardly placed logos, and other fishy elements should make spotting malicious emails a piece of cake.
Kimberly Gedeon, holding a Master's degree in International Journalism, launched her career as a journalist for MadameNoire's business beat in 2013. She loved translating stuffy stories about the economy, personal finance and investing into digestible, easy-to-understand, entertaining stories for young women of color. During her time on the business beat, she discovered her passion for tech as she dove into articles about tech entrepreneurship, the Consumer Electronics Show (CES) and the latest tablets. After eight years of freelancing, dabbling in a myriad of beats, she's finally found a home at Laptop Mag that accepts her as the crypto-addicted, virtual reality-loving, investing-focused, tech-fascinated nerd she is. Woot!

