Evil Malware Turns Antivirus Software Against PCs
A new proof-of-concept exploit known as DoubleAgent can not only hijack third-party Windows antivirus software, but use said software to deliver further attacks. While there’s no evidence that the exploit has made its way into the wild yet, most antivirus programs are still completely susceptible to it.
The entire point of antivirus software is to prevent malicious programs from compromising your system. But what happens when the malicious program in question can compromise your antivirus?
For now, only AVG , Malwarebytes and Trend Micro have patches available on coming soon. You could also just use a Linux or macOS instead of Windows, although they’re not entirely invulnerable, either. Or you could disable your existing third-party antivirus software and rely on Windows Defender, although it doesn't hold up well against zero-day malware.
MORE: Best Antivirus Software and Apps
This research into DoubleAgent comes from Cybellum, an Israeli cybersecurity company that specializes in zero-day exploits. Although DoubleAgent is an artificially constructed bit of malware, the flaw it preys upon is very much a zero-day vulnerability.
Windows uses a tool called Microsoft Application Verifier that helps software developers check for bugs in Windows-based programs. Every Windows program is subject to the Verifier’s scrutiny, including antivirus software.
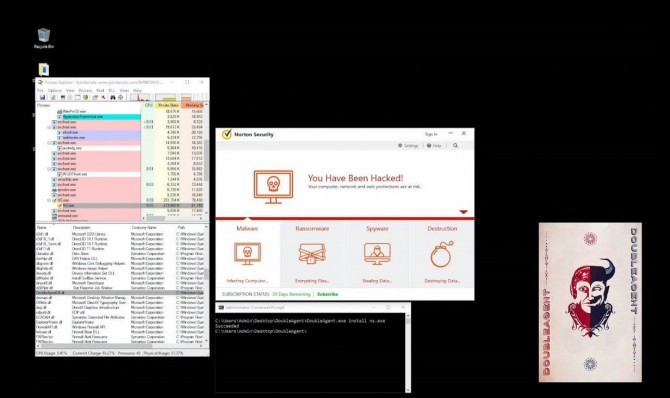
By crafting a phony registry key and a predatory DLL file for the Verifier to read, Cybellum was able to take full control over the Norton Security antivirus program. (A dynamic link library, or DLL, is a code repository that can used by more than one application. This attack uses the old "DLL hijack" technique to get an application to mistakenly load code from a malicious DLL.)
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
Cybellum even added a cheerful little skull graphic and the helpful message “You Have Been Hacked!” to Norton Security’s startup screen. Real hackers will probably not be so courteous.
Cybellum theorizes five possible attack vectors for cybercriminals using DoubleAgent. The first, and most obvious, scenario would be to turn the AV program itself into malware. A second, more subtle, method would be to leave the antivirus mostly alone, save for telling it to whitelist malware that malicious hackers want to spread. Similarly, a third method would tell the antivirus to ignore malicious remote activity, such as data-mining and decryption.
The other two methods are much less subtle, but just as devastating to the end-user. Antivirus programs often have top-level privileges, which would allow them to encrypt files or format a hard drive without the user’s permission. As such, antivirus software could be used as ransomware.
Finally, an attacker could make antivirus software flag and block any other application, causing a denial-of-service condition for just about any program on Windows, from an internet browser to a productivity tool. It’s not hard to see how an attack like this could cripple computers in a corporate setting, even if only for a day or two.
Remember, too, that DoubleAgent can compromise almost any program on Windows, not only antivirus software. Antivirus software, with its high system privileges, is just a quick and easy way to exploit this newly disclosed flaw.
“Since the DoubleAgent technique uses legitimate operating system mechanism to inject its code, it can’t be patched and this injection technique will live forever. So there is no notion of a patch,” the Cybellum blog noted.
Compromising a user’s antivirus program could theoretically be only the first step in a much more intricate attack. Microsoft does have a framework called Protected Processes that lets antivirus developers "sign" code to prevent such attacks -- but until very recently, only Microsoft's own Windows Defender program used it.
Cybellum shared its research with a number of antivirus companies. Vulnerable AV programs include those from Avast, AVG, Avira, Bitdefender, Trend Micro, Comodo, ESET, F-Secure, Kaspersky Lab, Malwarebytes, McAfee, Panda, Quick Heal and Norton.
Bleeping Computer reports that Malwarebytes, AVG and Trend Micro have either been patched, or will have a patch in the immediate future. Other companies are hopefully working on fixes, but there’s no guarantee that they’ll keep you safe.
As usual, keeping your antivirus software patched and up-to-date is your best defense against DoubleAgent. Even if your AV provider isn’t one of the three with a fix (almost) ready, it will probably get an update sooner rather than later. Since DoubleAgent isn’t out in the wild just yet, you probably have a little time before the attacks begin in earnest — if they ever do.