Why Windows 10 PCs are locking up and crashing after May update
Some users woke up to a serious bug on their machines after a recent Windows update.

Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You are now subscribed
Your newsletter sign-up was successful
Though Microsoft has already warned users that update support for Windows 10 will be sunsetted in October 2025, the operating system is still getting new patches.
But that’s not always a good thing, as some users around the web discovered after the latest KB5058379 cumulative update was released on May 13.
What is BitLocker, and how is it related to the buggy Windows update?
The reported problem involves the BitLocker function, native to most desktop and laptop builds of Windows 10.
BitLocker is designed as a security measure that encrypts entire drives at once, and often works in tandem with an internal chip called a Trusted Platform Module to verify the PIN, password, USB key, or 48-digit recovery key necessary to unlock the machine.
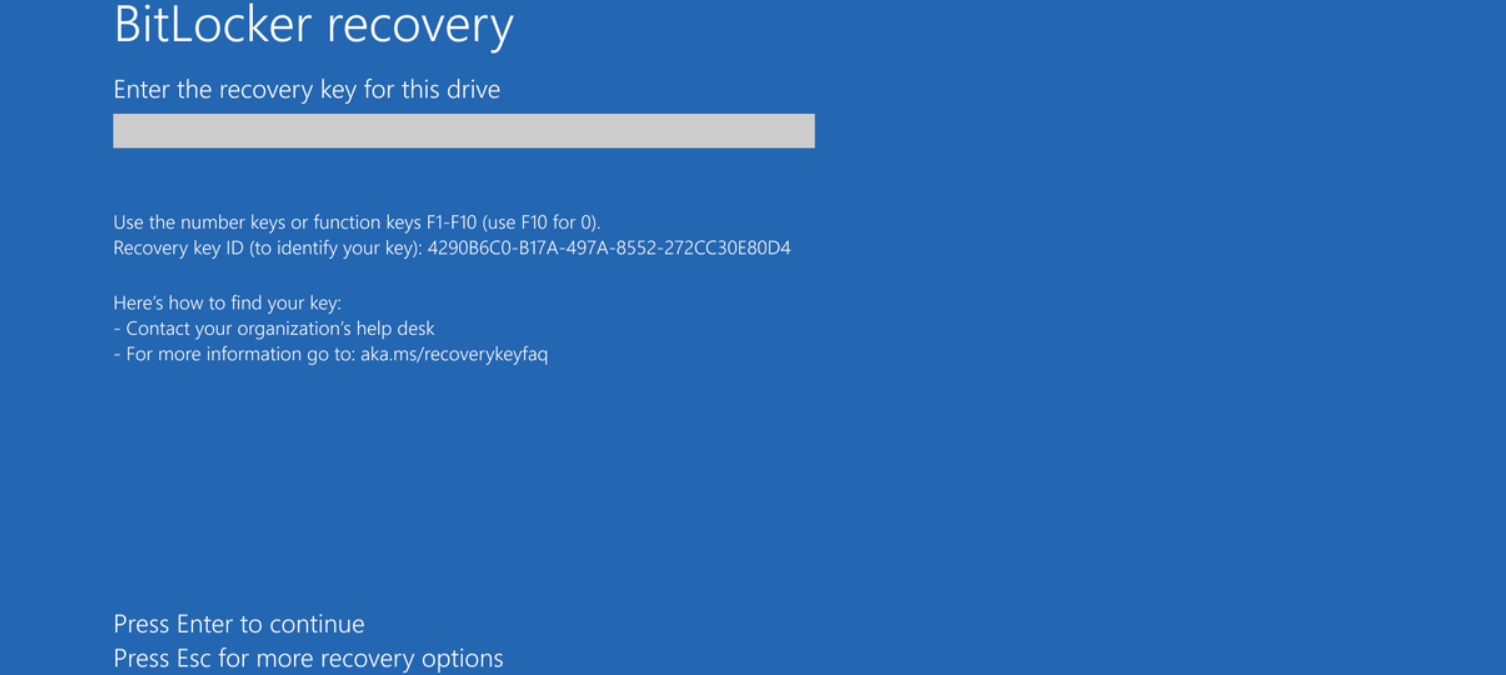
When a user sets this up on their own, they’re given a number of ways to regain access to their PC. The problem with this update is that BitLocker seems to get activated without any user input, and it will, therefore, lock them out of their machines on a system restart without any passwords or PIN numbers to get back in.
Key specs: 16-inch WUXGA (1920 x 1200) 300-nit touchscreen, AMD Ryzen 5 8540U 6-core CPU, 8GB RAM, AMD Radeon 740M Graphics, 512GB SSD.
Who is affected by the bad update?
So far, there hasn’t been a consistent enough thread to lock down who may or may not be vulnerable to the bug present in KB5058379. BleepingComputer has narrowed things to devices manufactured by either Dell, Lenovo, or HP, but others outside that circle have also reported issues of their own.
Microsoft employees have already responded to several users who reported their findings on Reddit. Though the bug has yet to be patched as of this writing on May 16th, the company has provided a workaround for the time being.
How do you get around the BitLocker bug and unlock your machine?
"According to Microsoft Support, these are the steps you should take if your machine has been affected by the BitLocker bug:
1. Disable Secure Boot
Access the system’s BIOS/Firmware settings.
Locate the Secure Boot option and set it to Disabled.
Save the changes and reboot the device.
2. Disable Virtualization Technologies (if issue persists)
Re-enter BIOS/Firmware settings.
Disable all virtualization options, including:
Intel VT-d (VTD)
Intel VT-x (VTX)
Note: This action may prompt for the BitLocker recovery key, so please ensure the key is available.
3. Check Microsoft Defender System Guard Firmware Protection Status
You can verify this in one of two ways:
Registry Method
Open Registry Editor (regedit).
Navigate to: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\SystemGuard
Check the Enabled DWORD value:
1 → Firmware protection is enabled
0 or missing → Firmware protection is disabled or not configured
GUI Method (if available)
Open Windows Security > Device Security, and look under Core Isolation or Firmware Protection.
4. Disable Firmware Protection via Group Policy (if restricted by policy)
If firmware protection settings are hidden due to Group Policy, follow these steps:
Using Group Policy Editor
Open gpedit.msc.
Navigate to: Computer Configuration > Administrative Templates > System > Device Guard > Turn On Virtualization Based Security
Under Secure Launch Configuration, set the option to Disabled.
Or via Registry Editor
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\SystemGuard]
"Enabled"=dword:00000000
Important: A system restart is required for this change to take effect.”
It’s also important to mention that you should only implement this workaround until Microsoft pushes a patched update. Disabling TXT in the BIOS could leave you or your administration’s systems much less secure than usual, so it should only be deployed if you absolutely need to access a machine affected by the bug.
Otherwise, the best bet is to wait until Microsoft resolves the issue and download anything recommended by Windows Update within the next few days.
Now, whether or not this coding cock up is the result of Microsoft's move to code upwards of 30% of Windows repositories using AI...who can say?
More from Laptop Mag

Chris Stobing grew up in the heart of Silicon Valley and has been involved with technology since the 1990s. Previously at PCMag, I was a hardware analyst benchmarking and reviewing consumer gadgets and PC hardware such as desktop processors, GPUs, monitors, and internal storage.
He's also worked as a freelancer for Gadget Review, VPN.com, and Digital Trends, wading through seas of hardware and software at every turn. In his free time, you’ll find Chris shredding the slopes on his snowboard in the Rocky Mountains where he lives, or using his culinary-degree skills to whip up a dish in the kitchen for friends.

