Hackers use Apple tools to infiltrate iPhones with malware — victim loses $20,000
Scam campaign CryptoRom abuses iOS TestFlight and WebClips to bypass Apple's App Store security
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You are now subscribed
Your newsletter sign-up was successful
Cybersecurity researchers have spotted new methods for scammers to infiltrate Apple's iPhone and use malware to swipe thousands of dollars, and the global cyber threat is still active.
Security software company Sophos reports a scam campaign dubbed CryptoRom is abusing iOS TestFlight and Apple WebClip to deploy fake mobile apps and websites, tricking users into installing malware. The scam was initially used in Asia, but has hit the U.S. and European victims since October 2021. Recently, a victim has reported losing $20,000, but the threat actors are expected to have stolen millions.
- Best antivirus apps in 2022
- Best password managers of 2022
- Best phone deals in 2022
As previously reported, threat actors use Apple's ad hoc distribution method, through distribution operations known as "Super Signature services," along with Apple's Enterprise Signature distribution scheme, to target victims. Now, the scam campaign is using other means including TestFlight Signature and WebClips to bypass the App Store’s security screening.
As Sophos states, TestFlight is used for testing the beta version of apps before they head to the App Store. It is used for small internal tests, sent out to 100 users by email, and public beta tests distributed to up to 10,000 users. The internal tests don't require an App Store security review, which is ideal for threat actors.
"Unfortunately, just as we’ve seen happen with other alternative app distribution schemes supported by Apple, “TestFlight Signature” is available as a hosted service for alternative iOS app deployment, making it all too simple for malware authors to abuse," stated Sophos researcher Jagadeesh Chandraiah. "These third-party services are extensively abused by CryptoRom authors."
TestFlight Signature only needs an IPA file to be sent, and the review process is "less stringent" than the App Store review, according to users. Sophos has spotted fake sites that disguised themselves as cryptocurrency mining firm BitFury peddling fake apps through Test Flight.
CryptoRom also used iOS WebClips to dupe iPhone users, as they were sent malicious URLs via the service. WebClips offers "fast access to favorite webpages or links, as Apple highlights, with Sophos stating that it can be used to make fake apps look more legit.
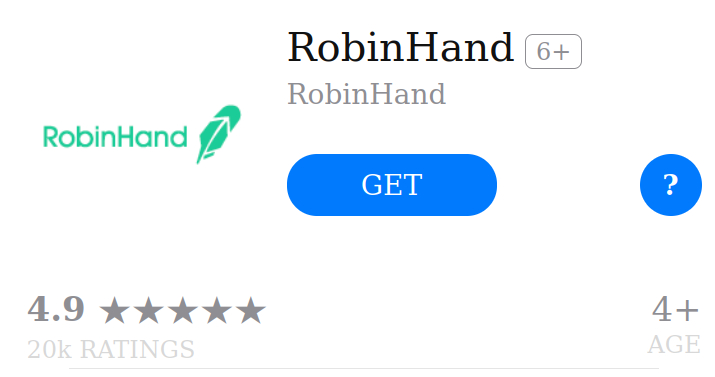
Chandraiah explains: "While investigating one of the CryptoRom URLs, we found related IPs that were hosting App store lookalike pages with a similar template, but with varying names and icons. The “apps” included one that mimics the popular Robinhood trading application, called ‘RobinHand.’ Its logo is similar to that of Robinhood."
For a better look at CryptoRom's hacking methods, check out the full Sophos Labs report. It's a good idea to keep your devices protected from malware threats, and the best antivirus apps can offer a helping hand. Plus, if you're wondering how to improve your Mac's security and privacy, we've got you covered.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.

Darragh Murphy is fascinated by all things bizarre, which usually leads to assorted coverage varying from washing machines designed for AirPods to the mischievous world of cyberattacks. Whether it's connecting Scar from The Lion King to two-factor authentication or turning his love for gadgets into a fabricated rap battle from 8 Mile, he believes there’s always a quirky spin to be made. With a Master’s degree in Magazine Journalism from The University of Sheffield, along with short stints at Kerrang! and Exposed Magazine, Darragh started his career writing about the tech industry at Time Out Dubai and ShortList Dubai, covering everything from the latest iPhone models and Huawei laptops to massive Esports events in the Middle East. Now, he can be found proudly diving into gaming, gadgets, and letting readers know the joys of docking stations for Laptop Mag.