"Chat GPT" scam extension stole Facebook data from up to 9,000 users
FakeGPT should be a lesson to us all
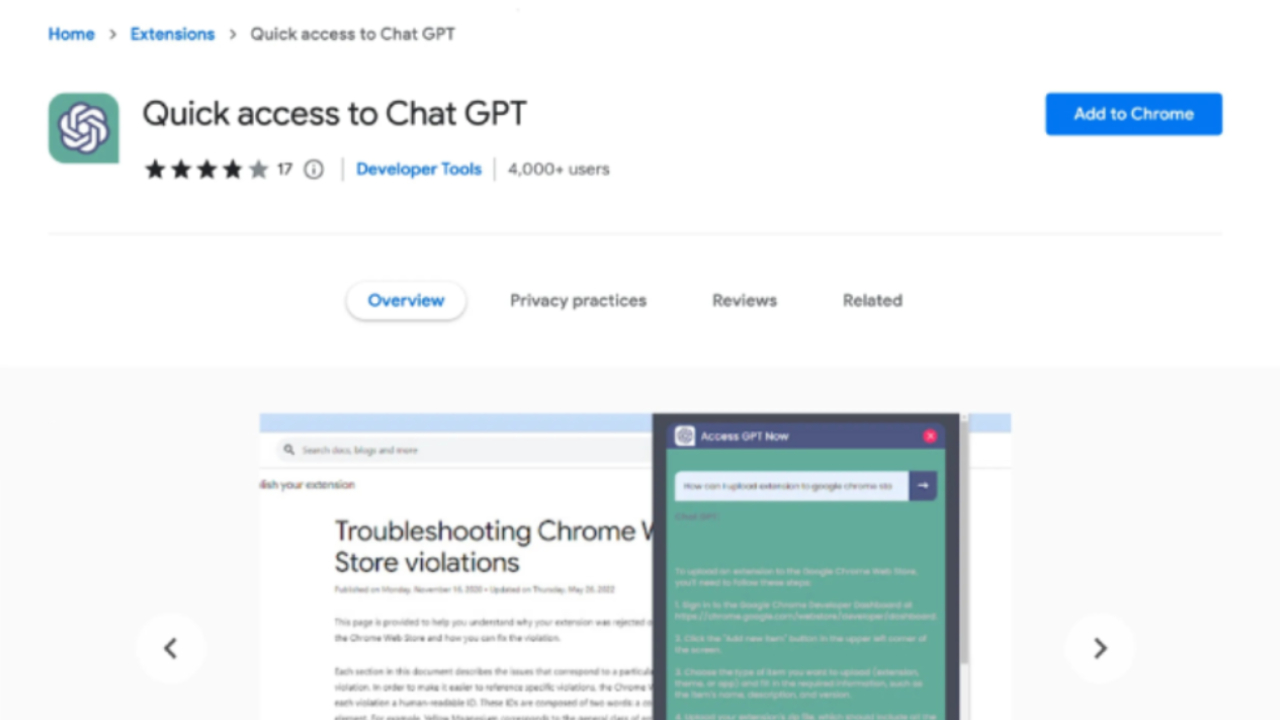
Chat GPT for Google, a malicious Google extension that is named similarly to the official ChatGPT for Google extension, has been taken off the Chrome store after it stole Facebook data from up to 9,000 downloaders who were none-the-wiser.
This malicious extension was not only riffing off the official extension's name, but it's also based on the same source code used by the real ChatGPT for Google. This was initially discovered by Guardio, a information security service that had found this extension was installing hidden backdoors to give admin permissions to malicious sources.
"FakeGPT" runs rampant
Advertisements on Facebook were paid for by those same malicious actors, promoting something called "Quick access to Chat GPT" while an army of bots who were already hijacked by the application used their "ad account credits" to further prop up FakeGPT. By hijacking high-profile Facebook business accounts, this created a quick and easy cycle of positive results for the malicious party.
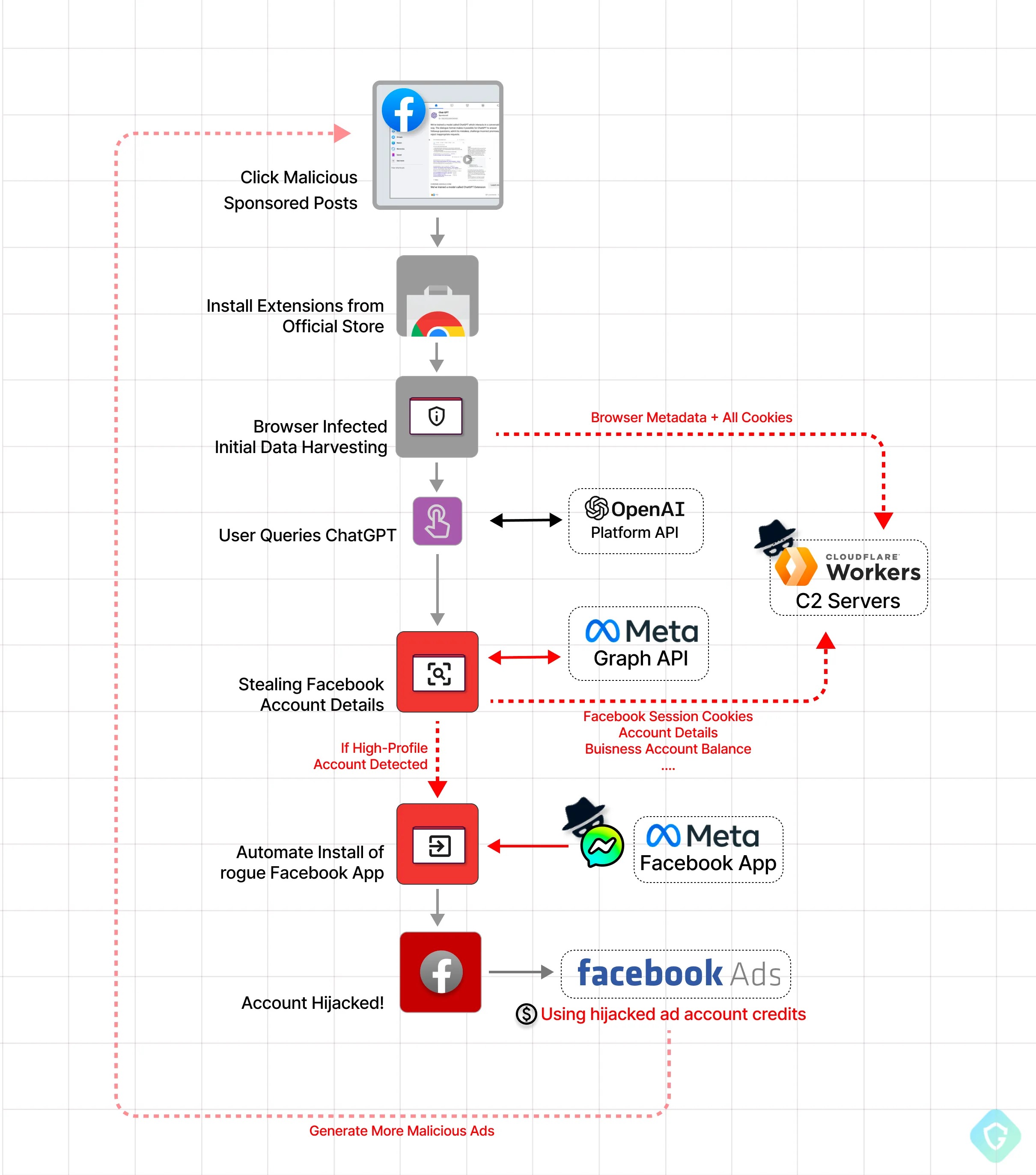
The end result? More and more Facebook accounts getting hijacked. But the real question remains, what were Facebook and Google doing in the face of this? How were these malicious parties so easily able to not only advertise data-stealing software on Facebook itself, but also get accepted as a real extension in Chrome's store?
Users should have certainly been more careful, but there is negligence on the part of these enormous companies who didn't snuff out the software before it became publicly available.
Moral of the story is: Advertisements are not to be trusted, even on reputable websites. And just because something is available on an official app store, doesn't mean it's legit. We all need to practice internet safety to ensure we're not victims.
Google needs to pay attention
Chat GPT for Google needs to be a lesson to the company. How did this thing get accepted into the official Chrome extension store? Users should have a level of internal comfort knowing that if they install something from the official Chrome marketplace, they won't have to worry about malicious attacks.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
Google should work on its curation and be a little stricter about what gets accepted, at least insofar as ensuring nothing that is put onto the store is going to compromise its users. For now, however, all we can do is try to be a little safer in the face of these attacks.

Self-described art critic and unabashedly pretentious, Claire finds joy in impassioned ramblings about her closeness to video games. She has a bachelor’s degree in Journalism & Media Studies from Brooklyn College and five years of experience in entertainment journalism. Claire is a stalwart defender of the importance found in subjectivity and spends most days overwhelmed with excitement for the past, present and future of gaming. When she isn't writing or playing Dark Souls, she can be found eating chicken fettuccine alfredo and watching anime.