MacBook users beware! Hackers are buying $49 malware to wreak havoc on macOS
Hackers are paying $50 to execute malicious files on macOS

Millions of MacBooks could be in trouble. According to a new report from Check Point Research (CPR), hackers are shelling out $50 to purchase a malware strain from the dark web that wreaks havoc on macOS systems.
The malware strain, dubbed "XLoader," lets cybercriminals harvest log-in credentials, grab screenshots, log keystrokes and execute malicious files.
XLoader, a macOS malware strain, is an offshoot of a Windows bug
XLoader, a nasty new malware strain that targets macOS, is a derivative of the notorious "Formbook" trojan, which was designed to steal personal data from Windows PCs. Formbook disappeared in 2018, but according to CPR investigators, it was rebranded to XLoader in 2020.
"Over the past six months, CPR studied XLoader’s activities, learning that XLoader is prolific, targeting not just Windows, but to CPR’s surprise, Mac users as well," the report said.
MacBooks have a reputation for keeping malware at bay, but this isn't entirely true, according to Check Point Software's Head of Cyber Research Yaniv Balmas. Sure there's a gap between Windows and macOS in terms of malware vulnerability (the former is more susceptible), but the gap is closing over time.
"The truth is that MacOS malware is becoming bigger and more dangerous. Our recent findings are a perfect example and confirm this growing trend," he said. Balmas added that cybercriminals are more interested in the macOS platform as it increases in popularity, and as result, he anticipates more macOS threats in the future.
How does XLoader work?
XLoader, a new member of the Formbook family, sneaks its way into macOS devices by luring victims into downloading and opening malicious files from spoofed emails; these attachments appear to be Microsoft Office documents.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
Cybercriminals can purchase XLoader licenses from the dark web for as low as $50. As mentioned, once a hacker gets their hands on XLoader, they can use it to collect victims' log-in credentials, execute malicious code, grab screenshots and log keystrokes.
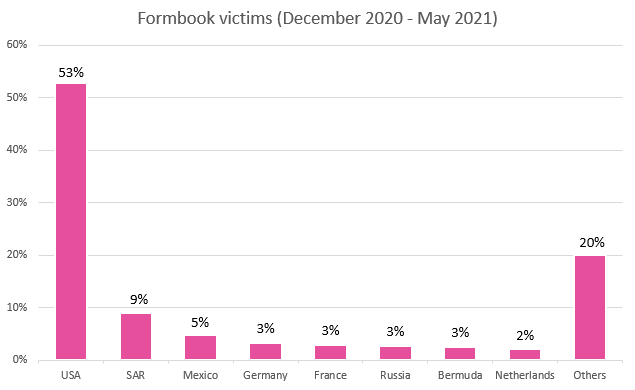
CPR investigators tracked XLoader activity between December 2020 and June 2021, and as a result, they discovered that more than half of XLoader victims reside in the United States.
The report urges macOS and Windows users to avoid opening suspicious attachments and visiting fishy websites. CPR also recommends anti-malware software to avoid infection.
"I would think twice before opening up any attachments from emails I get from senders I don’t know," Balmas said.
Kimberly Gedeon, holding a Master's degree in International Journalism, launched her career as a journalist for MadameNoire's business beat in 2013. She loved translating stuffy stories about the economy, personal finance and investing into digestible, easy-to-understand, entertaining stories for young women of color. During her time on the business beat, she discovered her passion for tech as she dove into articles about tech entrepreneurship, the Consumer Electronics Show (CES) and the latest tablets. After eight years of freelancing, dabbling in a myriad of beats, she's finally found a home at Laptop Mag that accepts her as the crypto-addicted, virtual reality-loving, investing-focused, tech-fascinated nerd she is. Woot!

