Zoom security flaw exposed — hackers could use this feature for phishing attacks (Update)
Zoom says it's already patched the vulnerability

Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You are now subscribed
Your newsletter sign-up was successful
Update on July 16: A Zoom spokesperson reached out to Laptop Mag to reassure users that the security issue has been fixed: “Zoom has addressed the issue reported by Check Point and put additional safeguards in place for the protection of its users. Zoom encourages its users to thoroughly review the details of any meeting they plan to attend prior to joining, and to only join meetings from users they trust. We appreciate Check Point notifying us of this issue." The spokesperson also encouraged users to send detailed reports of all security-flaw discoveries to security@zoom.us
Zoom just can't win. The videoconferencing platform — plagued with security issues and PR disasters — was on a path to redemption. But Check Point Research, a cybersecurity firm, poked another hole in Zoom's already fragile reputation.
Capitalizing on Zoom's vanity URL feature, Check Point researchers discovered that hackers could pose as trusted individuals to phish for sensitive information.
- Zoom gets a new game-changing feature -- goodbye, Google Meet
- Zoom vs. Teams: Which video conferencing app is right for you?
- Zoom update 5.0 fixes nasty security issues: How and when to get it
How hackers could use Zoom's vanity URL feature for phishing attacks
Zoom's vanity URL feature allows business users to create custom URLs for their organization. For example, if we created a vanity URL with Zoom, it would be LaptopMag.zoom.us.
Prior to Zoom's fix, a hacker could manipulate ID meeting links and pose as a fellow employee. Appearing to be a legitimate member of the organization, the attacker could send invitations to a victim, which could provide a gateway for the hacker to steal credentials and sensitive information.
In other words, a hacker would have been able to generate a standard meeting link on Zoom (e.g. https://zoom.us/j/67844124) and simply tack on the organization's business name in front of the URL (e.g. LaptopMag.zoom.us/j/67844124). The URL would still work to the attacker's delight. The hacker could email this manipulated link to employees of a targeted organization, entice them to join the Zoom session and phish for sensitive information.
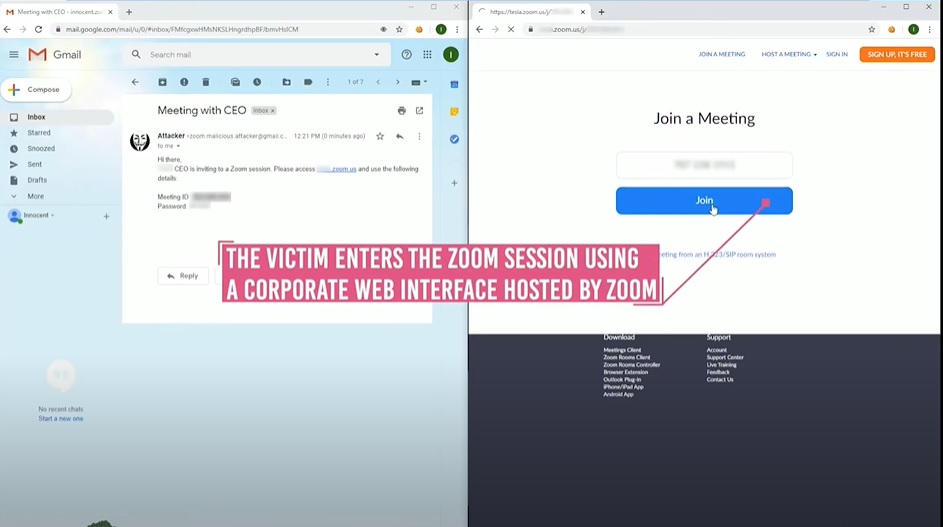
"Without particular cybersecurity training on how to recognize the appropriate URL, a user receiving this invitation may not recognize that the invitation was not genuine or issued from an actual or real organization," Check Point Research investigators wrote.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
Zoom has resolved the vanity URL issue
Thankfully, Zoom has quickly nipped the issue in the bud.
"All the details of how an attacker could impersonate an organization’s Zoom subdomain links or actual sub-domain website discussed here were responsibly disclosed to Zoom Video Communications, Inc. as part of our ongoing partnership and cooperation. This security issue has been fixed by Zoom, so the exploits described are no longer possible," the Check Point researchers added.
The last thing Zoom needs is another security vulnerability to rattle its reputation in the press. The super-popular videoconferencing platform is expanding into the hardware market, according to TheVerge, with a $600 device called Zoom For Home — DTEN ME.
DTEN ME is a 27-inch, 1080p touchscreen display that is equipped with three smart webcams and eight built-in, noise-reducing microphones. The device also comes with pre-installed Zoom software.
Considering Zoom's cringe-worthy history of security flaws, some folks may be apprehensive about bringing a Zoom device into their home. The company must continue working on rebuilding its trust with consumers to win over the hardware market.
Kimberly Gedeon, holding a Master's degree in International Journalism, launched her career as a journalist for MadameNoire's business beat in 2013. She loved translating stuffy stories about the economy, personal finance and investing into digestible, easy-to-understand, entertaining stories for young women of color. During her time on the business beat, she discovered her passion for tech as she dove into articles about tech entrepreneurship, the Consumer Electronics Show (CES) and the latest tablets. After eight years of freelancing, dabbling in a myriad of beats, she's finally found a home at Laptop Mag that accepts her as the crypto-addicted, virtual reality-loving, investing-focused, tech-fascinated nerd she is. Woot!

