Devastating Bluetooth flaw leaves millions of PCs open to malicious attacks
A nasty Bluetooth bug renders your laptop insecure

Who doesn't love Bluetooth?
That mesmerizing blue light comes on, and data or audio can be exchanged between devices on a wavelength. But a team of researchers found that Bluetooth isn't as innocuous as it seems -- this wireless tech can open the window to malicious hackers, our sister site Tom's Guide reported.
- Zoom update 5.0 fixes nasty security issues: How and when to get it
- HP security flaw could leave millions of PCs open to attack: What to do
- Windows 10 'critical' flaw is being actively exploited: What to do
How the Bluetooth flaw affects your PC
Investigators from École Polytechnique Fédérale de Lausanne in Switzerland published findings of a newly discovered flaw that lets hackers connect to your Bluetooth-enabled device by, in simple terms, impersonating a previously paired and trusted Bluetooth peripheral.
The hacking method is called Bluetooth Impersonation Attacks (BIAS). The vulnerability lies within Bluetooth's bonding method. When two Bluetooth devices are paired for the first time, they exchange something called a "long-term key," which will be stored for future connections with the peripheral.
To make their report more digestible, researchers called the master device "Bob" (e.g. your laptop), named the peripheral "Alice" (e.g. a speaker) and called the hacker "Charlie." In short, Bluetooth double-checks to make sure both Alice and Bob have a shared long-term key. Bluetooth also verifies Alice and Bob's address.
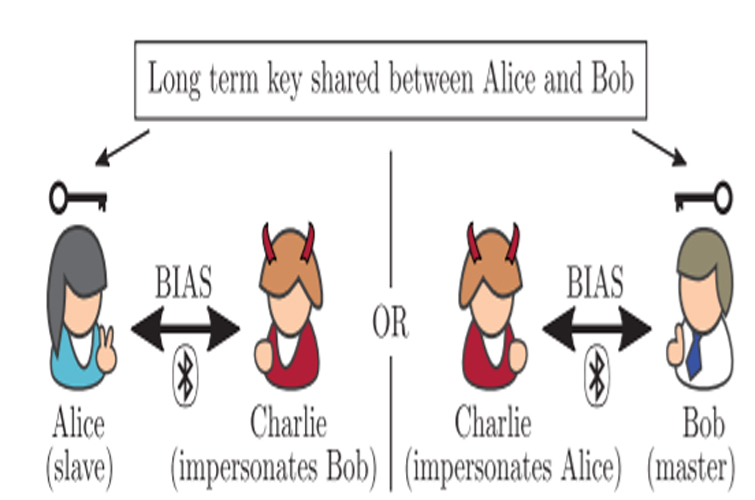
However, big-and-bad Charlie can come barging in by connecting with Alice, the peripheral, pretending to be her good ol' trusted friend Bob -- and Alice will fall for it.
"As the Bluetooth standard does not mandate to use of the legacy authentication procedure mutually while establishing a secure connection, Alice does not have to authenticate that Charlie knows the long-term key," the study wrote.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
The researchers warned that Charlie the Hacker doesn't have to be present when one's laptop is connecting to a peripheral to launch the BIAS method and infiltrate the victim's device.
Who is at risk for Bluetooth Impersonation Attacks?
The researchers tested Cypress, Qualcomm, Apple, Intel, Samsung and CSR chips and performed experiments on the following laptops: MacBook Pro, ThinkPad L390, ThinkPad X1 Carbon (3rd Gen), HP ProBook 430 G3, ThinkPad 41U5008, Lenovo IdeaPad U430 and ThinkPad X230. All of these devices were vulnerable to the BIAS attack.
The flaws do not lie in the aforementioned devices themselves, but rather the Bluetooth chips that are embedded in them, which can be found across a vast array of laptop models.
Can you protect yourself from Bluetooth Impersonation Attacks?
According to the BIAS website, consumers should expect all their standard-compliant Bluetooth devices to be vulnerable to hacking. The researchers noted that some laptop vendors may have implemented "workarounds" for the Bluetooth vulnerability after they revealed the BIAS hacking method to the industry in December 2019.
"So the short answer is: if your device was not updated after December 2019, it is likely vulnerable. Devices updated afterward might be fixed," the investigators said.
On the plus side, the Bluetooth Special Interest Group, an organization that oversees the wireless standard, said it planned on correcting this Bluetooth flaw to make future connections more secure.
Kimberly Gedeon, holding a Master's degree in International Journalism, launched her career as a journalist for MadameNoire's business beat in 2013. She loved translating stuffy stories about the economy, personal finance and investing into digestible, easy-to-understand, entertaining stories for young women of color. During her time on the business beat, she discovered her passion for tech as she dove into articles about tech entrepreneurship, the Consumer Electronics Show (CES) and the latest tablets. After eight years of freelancing, dabbling in a myriad of beats, she's finally found a home at Laptop Mag that accepts her as the crypto-addicted, virtual reality-loving, investing-focused, tech-fascinated nerd she is. Woot!

