3 Android apps are stealing banking info via screen recording — remove them ASAP before you're next
Hackers will stop at nothing to snatch your hard-earned money

Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You are now subscribed
Your newsletter sign-up was successful
In case you missed it, cybersecurity firm ThreatFabric published a report last Friday regarding its discovery of five malicious Google Play apps masquerading as legitimate services, including finance tracking and calculating taxes.
The quintet of apps fall under two relatively new malware families: Vultur and Sharkbot. And yes, they're every bit as vicious as they sound (h/t GreenBot).
The five apps you must remove ASAP
Let's start with the malicious trio of apps that stem from the villainous Vultur family: My Finances Tracker: Budget, C, Zetter Authenticator, and Recover Audio, Images & Videos. The three apps attracted 1,000+, 10,000+ and 100,000+ downloads respectively.
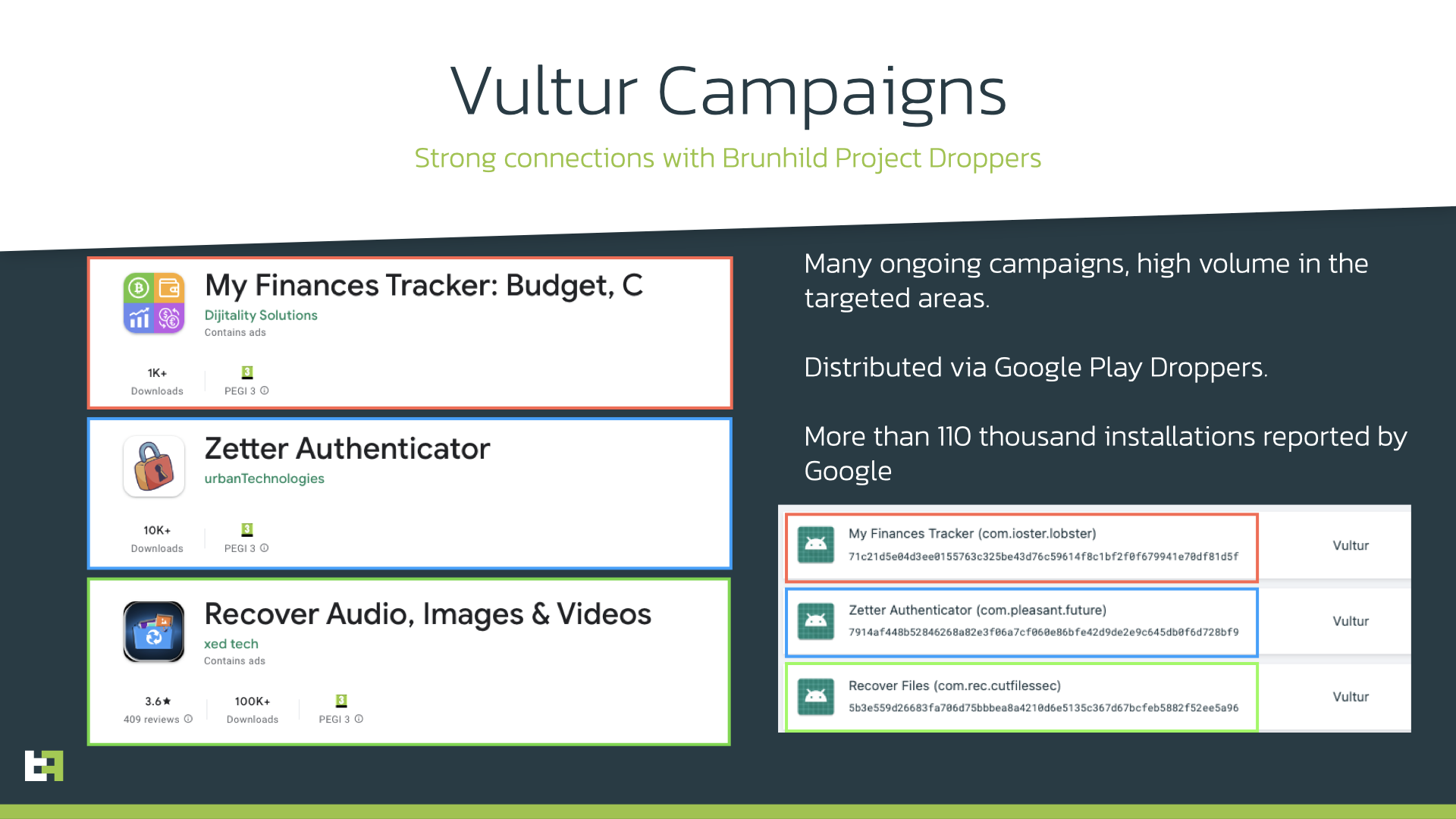
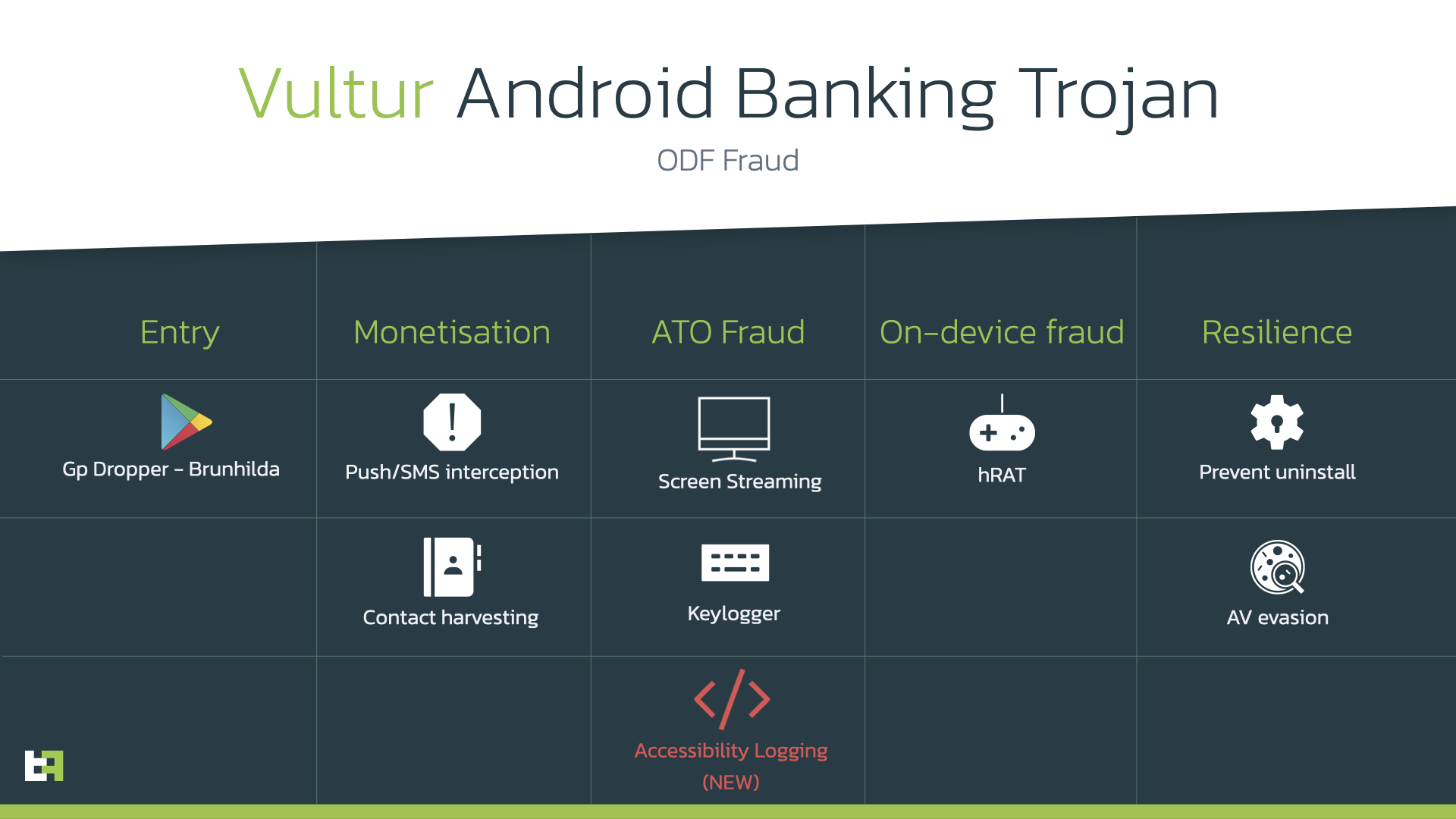
You may be wondering, "What, exactly, is Vultur malware?" According to the cybersecurity report, Vultur was first discovered in July 2021. It's an Android banking trojan that steals personally identifiable information (PII) by recording your screen.
"It is also able to create a remote session on the device using VNC technology to perform actions on the victim's device, effectively leading to On-Device Fraud (ODF)," the ThreatFabric report said.
Interestingly, ThreatFabric discovered a new, concerning modus operandi with the three aforementioned Vultur-injected Google Play apps. Not only does it rely on screen streaming to steal information from unwitting victims, but it also utilizes accessibility logging. In other words, the trio of apps can track your gestures and taps to spy on your data.
If that wasn't creepy enough, ThreatFabric also unveiled its findings regarding two apps under the Sharkbot malware family: Codice Fiscale 2022 and File Manager, Lite. The former app targets Italian users while the latter targets Italian and UK quarries. However, ThreatFabric warns that Android users shouldn't get too comfortable.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
"The payload delivered [from Codice Fiscale 2022 and File Manager, Lite] still has banks from Italy, UK, Germany, Spain, Poland, Austria, US, and Australia in its target list," the report said.
What's fearsome about this new Sharkbot iteration is that, unlike previous campaigns, this one slips under the radar more easily because it does not prompt users to accept suspicious, fishy permissions.
When Sharkbot gets its fins on a device, it can steal users' banking account credentials and even slip through multi-factor authentication barriers. Despite Google's policy and security changes, dangerous malware still finds a way to wiggle its way into the Play Store.
"Google Play still remains the most 'affordable' and scalable way of reaching victims for most of the actors of different level," ThreatFabric concluded.
Kimberly Gedeon, holding a Master's degree in International Journalism, launched her career as a journalist for MadameNoire's business beat in 2013. She loved translating stuffy stories about the economy, personal finance and investing into digestible, easy-to-understand, entertaining stories for young women of color. During her time on the business beat, she discovered her passion for tech as she dove into articles about tech entrepreneurship, the Consumer Electronics Show (CES) and the latest tablets. After eight years of freelancing, dabbling in a myriad of beats, she's finally found a home at Laptop Mag that accepts her as the crypto-addicted, virtual reality-loving, investing-focused, tech-fascinated nerd she is. Woot!

