An 18-year-old browser exploit leaves MacBooks and Linux laptops vulnerable — but a fix is coming
It affects Chromium, Firefox, and Safari on laptops running macOS and Linux.

Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You are now subscribed
Your newsletter sign-up was successful
Sometimes, we've seen big companies take up to a few months to fix a glaring bug, risk, or other issue within an OS or a browser, but usually, issues are fixed within days or weeks. However, a vulnerability recently brought up by Oligo Security has gone without a fix for much longer: 18 years.
It affects Chromium, Firefox, and Safari on laptops running macOS and Linux.
This vulnerability — referred to by Oligo as the "0.0.0.0 Day" vulnerability—allows for remote code execution via a local network through a public website. And here's the scary part: it affects Chromium, Firefox, and Safari on laptops running macOS and Linux.
Malicious websites can navigate through weak browser security, an issue Oligo says "stems from the inconsistent implementation of security mechanisms across different browsers, along with a lack of standardization in the browser industry."
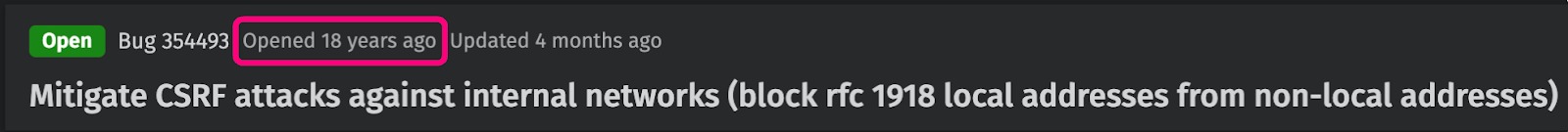
Oligo stumbled across a security issue reported to Mozilla in 2006 that's still open today, unfixed, despite multiple major issues between then and now. According to Oligo, "The bug report was closed, reopened, then prioritized—and will now remain open until Firefox implements [Private Network Access]."
So what are big companies planning to do to address this seemingly major flaw in browsers?
Major browsers respond to "0.0.0.0 Day" vulnerability
Chrome is the most popular browser, so it's good news that Google already has a plan to "block access to IP address 0.0.0.0 in advance of [Private Network Access] completely rolling out."
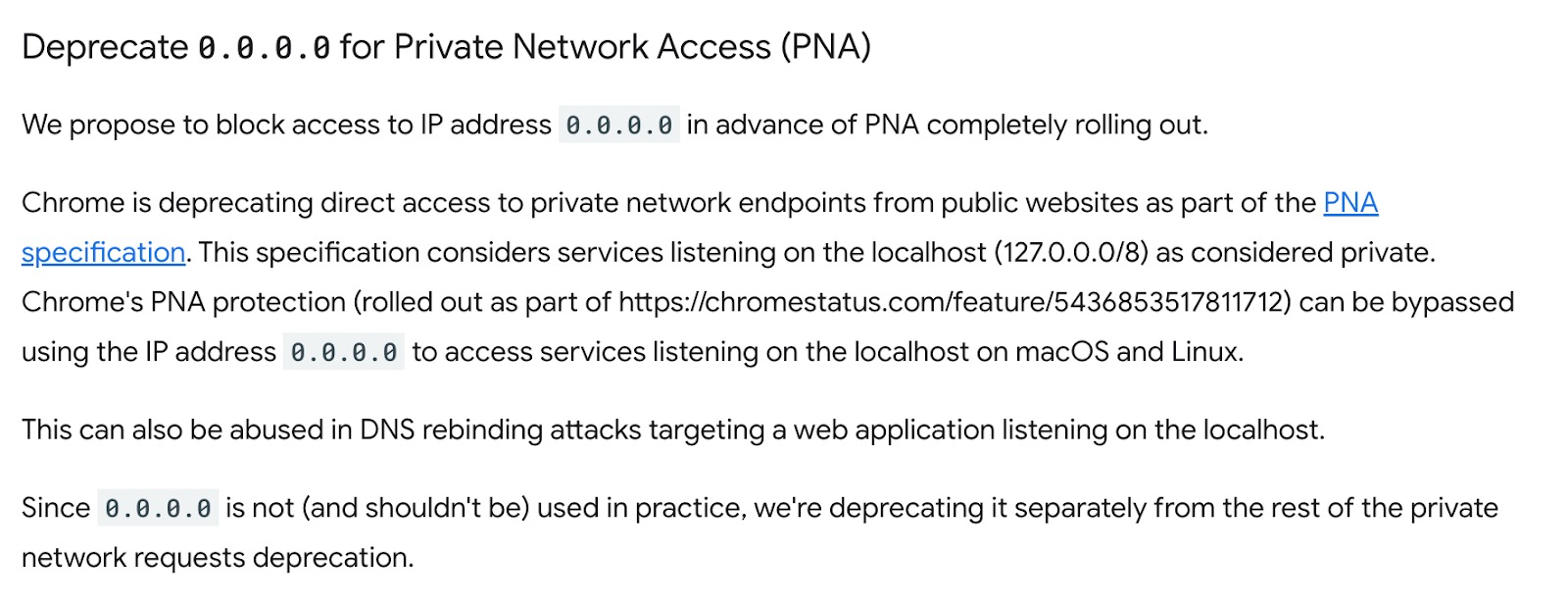
This blocked access will start rolling out with Chromium 128, released in beta on July 24. The company hopes to have it ready to ship by Chrome 133. Once it officially rolls out, the exploited IP address will be entirely blocked to Chrome and Chromium users.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
According to Oligo, Apple has issued "breaking changes to WebKit that block access to 0.0.0.0," those updates can be viewed on GitHub.
However, Mozilla's plans to address the issue are a bit more uncertain. Oligo says Mozilla updated the Fetch specification to block the IP address and has "prioritized implementation of Private Network Access, but it is not implemented yet."
A Mozilla spokesperson tells PCMag that "Imposing tighter restrictions comes with a significant risk of introducing compatibility problems," following up with, "As the standards discussion and work to understand those compatibility risks is ongoing, Firefox has not implemented any of the proposed restrictions."
On Wednesday, Microsoft updated the Microsoft Edge Security Updates page to read: "Microsoft is aware of the recent Chromium security fixes. We are actively working on releasing a security fix."
Hopefully, over the next few months (or even better, weeks), this massive vulnerability affecting all major browsers will be fixed.

Sarah Chaney is a freelance tech writer with five years of experience across multiple outlets, including Mashable, How-To Geek, MakeUseOf, Tom’s Guide, and of course, Laptop Mag. She loves reviewing the latest gadgets, from inventive robot vacuums to new laptops, wearables, and anything PC-related. When she's not writing, she's probably playing a video game, exploring the outdoors, or listening to her current favorite song or album on repeat.









