Malware hiding in browser extensions attacks millions — delete it now
Malicious browser extensions have affected nearly 7 million users since 2020

Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
You are now subscribed
Your newsletter sign-up was successful
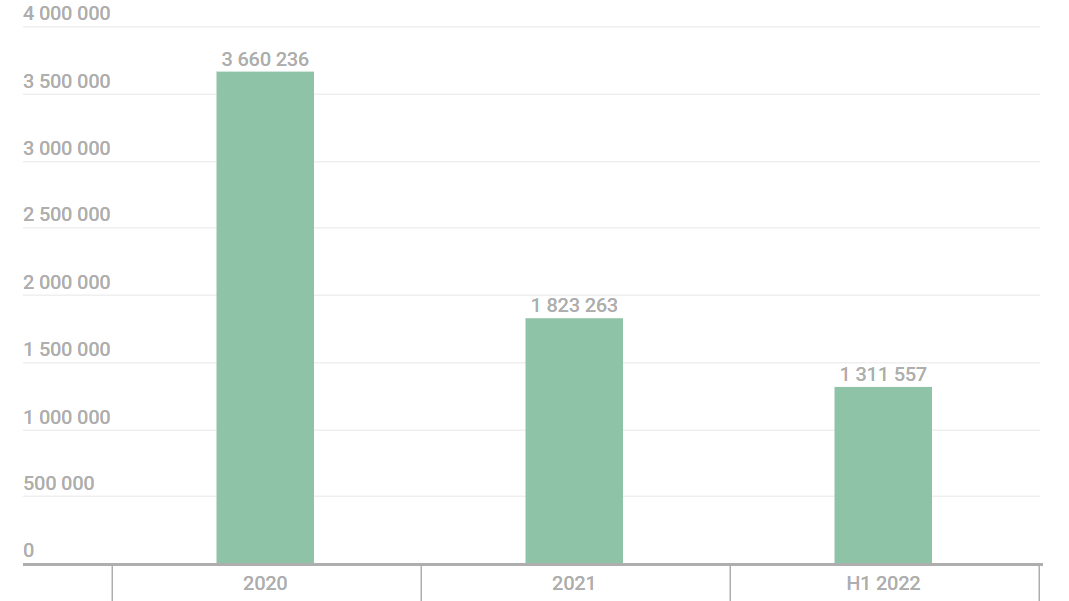
Cybersecurity analysts observed users unknowingly downloading malicious browser extensions hiding threats including adware and malware, with over 1.3 million users already being attacked in 2022.
Research from cybersecurity provider Kaspersky found nearly 7 million users being affected by unwanted software disguised as browser add-ons, with many being found on Google Chrome. As reported, 4.3 million unique users were attacked by adware sneaking their way onto systems, while over 2.6 million users were affected by malware.
The threat statistics were taken between January 2020 and June 2022, with the online security company stating that 1,311,557 users have already been affected during the first half of this year — more than 70% of affected users from all of 2021. It's important to note that these results were taken from Kaspersky's own security network shared by users, meaning these numbers could be far higher.
Four of the most popular threats hiding as browser extensions were noted, including malicious browser extension family FB Stealer. This year alone, 3,077 unique users were detected having downloaded the malware. As the name implies, it can steal user credentials from Facebook, giving hackers access to valuable information such as emails, passwords, and even financial information.
The malware is hard to spot, as once it's added to the browser, it will mimic the Google Translate Chrome extension. It spreads to users through a trojan known as "NullMixer," which acts as a software installer.
The extension changes the default search engine and extracts Facebook session cookies, sending them to the hacker's servers. Once done, threat actors have the ability to log into a user's Facebook account and then change their login details, leaving them able to masquerade as the user and steal information.
Beware of adware
While malware hiding in browser extensions has been a major issue, adware has been used as the most common threat. Adware is a way for threat actors to generate revenue by automatically displaying an obnoxious number of online advertisements on a user's screen, and the report shows the rise in deploying it through browser add-ons.
Some of the biggest threats include the WebSearch adware family, with 876,924 users being affected by it.
"WebSearch extensions change the browser’s start page so that, instead of the familiar Chrome page, the user sees a minimalistic site consisting of a search engine and several links to third-party resources, such as AliExpress or Farfetch," the report states.
With the new affiliate links, threat actors can profit from ad revenue the more these links are used. Plus, using the default search engine means collecting user data, with the relevant ads according to a search then popping up in search results.
Another threat includes DealPly-related extensions, which saw 97,515 users being affected. It's a popular tool among cybercriminals, and is often downloaded through hacked software from sketchy sites. Like WebSearch, it changes the home page with affiliate links and a default search engine.
Finally, AddScript is another adware threat family, with 156,698 being affected. As the report states, this extension can be used to music and videos from social networks or proxy managers.
"When the extension is running, it contacts a hardcoded URL to get the C&C server address. It then establishes a connection to the C&C server, receives malicious JavaScript from it, and runs it covertly. The only way the user can notice the execution of third-party instructions is by the increased consumption of processor power."
AddScript can run unwanted videos on a user's PC, all so threat actors can gain money from the video views. But it can also be used for "cookie dropping," which adds cookies despite that user not clicking on any affiliate links. As Kaspersky puts it: "fraudsters trick websites into thinking they have sent them traffic without actually doing so."
Stay protected
You’ll know when your device is infected with malware or adware through a number of different signs. Of course, the most glaring indication is the abundance of ads that pop up on your PC, tablet, or phone. But it could also mean a change in your web browser’s homepage and default internet search, a new toolbar, and web pages not displaying the way they used to.
Stay away from downloading browser extensions from unofficial or suspicious-looking websites, and stick to Chrome's official web store or the store of the browser you are using.
For more about getting rid of adware and all kinds of adware, check out how to remove adware. And, to make sure your device is safe from any kind of malware, be sure to check out the best antivirus apps.
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.

Darragh Murphy is fascinated by all things bizarre, which usually leads to assorted coverage varying from washing machines designed for AirPods to the mischievous world of cyberattacks. Whether it's connecting Scar from The Lion King to two-factor authentication or turning his love for gadgets into a fabricated rap battle from 8 Mile, he believes there’s always a quirky spin to be made. With a Master’s degree in Magazine Journalism from The University of Sheffield, along with short stints at Kerrang! and Exposed Magazine, Darragh started his career writing about the tech industry at Time Out Dubai and ShortList Dubai, covering everything from the latest iPhone models and Huawei laptops to massive Esports events in the Middle East. Now, he can be found proudly diving into gaming, gadgets, and letting readers know the joys of docking stations for Laptop Mag.